In the following I will try to show how to generate user certificates on e-tokens by using the Windows CA. This tokens can be used after that for secure user authentication or signing.
Prerequisites:
– Install the Windows CA service. This comes a standard feature in Windows Server 2012.
– Internet Explorer 9 and up on the client machine
– Make sure to enable active scripting for the security zone to which the enterprise CA belongs (see https://support.microsoft.com/en-us/kb/939290)
– install SafeNet Authentication Client
– empty e-tokens
– If using a remote client to access the CA server web interface then the token must be inserted in the client machine USB port. Note that is this case “SafeNet Authentication Client” must be installed also on the client machine
– If working directly on the CA server the token must be inserted in the CA server USB port and “SafeNet Authentication Client” must be installed also on the CA server
The CA machine controls the certificate issuing process, and is located in a restricted area with no network connections. The issuing process is as follows:
STEP 1:
Open Internet Explorer (e.g. by clicking on IE Shortcut on your Desktop)
Access the CA by typing the URL as follows: http://CA_IP/certsrv
STEP 2:
Click Request a certificate
STEP 3:
Click Advanced Certificate Request
STOP 4:
Click Create and submit a request to this CA
STEP 5:
Select the following options:
Intended purpose: ‘Client Authentication Certificate’
Name: Username from Enterprise Systems.
Do not complete the email field
Company: name of the client organization
CSP: Select ‘eToken Base Cryptographic Provider’
Key Usage: Select ‘both’
Key Size: Select 2048 bit
Select ‘Enable strong private key protection’
Click Submit
STEP 6:
Insert a blank eToken
You are prompted to input the eToken password. Type 1234567890 (default value).
STEP 7:
Go to the CA, and open the Certificate Authority (Start/Programs/Administrative Tools/Certification Authority)
Go to Pending Requests folder, and issue the pending certificate.
Record the ID of the certificate being issued.
STEP 8:
Open Internet Explorer again and access the URL as above.
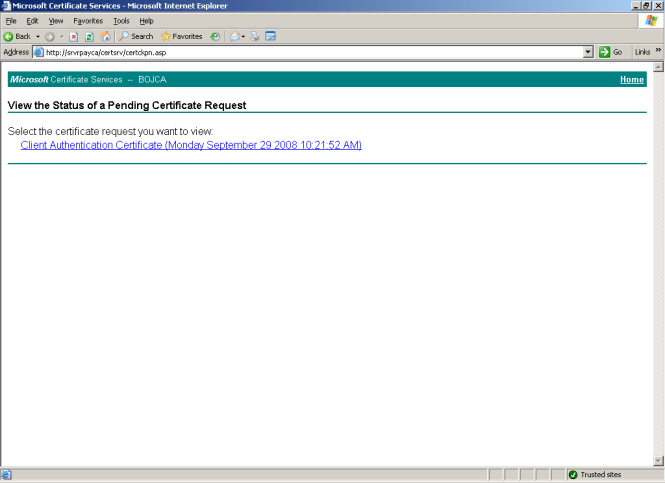
STEP 9:
Select ‘View the status of a pending certificate request’
STEP 10:
Click the pending request
STEP 11:
Click Install this certificate.
NOTE: The ID number of the certificate and the serial number of the eToken should be recorded in a logbook. The name of the user/participant bank should also be recorded for reference purposes.